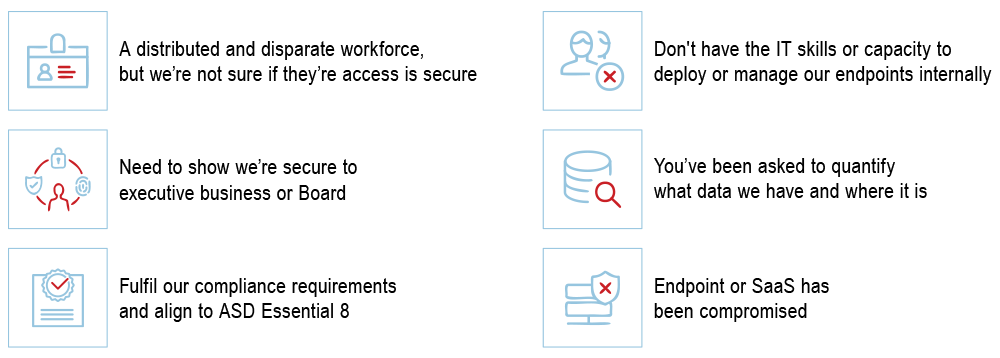
Secured Endpoint Management for empowered Australian workforces.
As work from anywhere becomes the norm, networks are being exposed to endless endpoints. Our Research on Endpoint Management shows that 70% of successful cyber breaches originate with an endpoint user device.
A more distributed workforce means companies are forced to rethink or relax their BYOD and home Wi-Fi restrictions—exposing their network to threats.