Australia, a top digital technology leader, faces a cybercrime every 7 minutes, highlighting the need for robust network security. Secure Access Service Edge (SASE) and Security Service Edge (SSE) are increasingly popular for enhancing security and network performance. Though both aim to safeguard digital assets, they offer distinct methods and features. This discussion will delve into the key differences between SASE and SSE, helping you determine the best fit for your organisation's security needs.
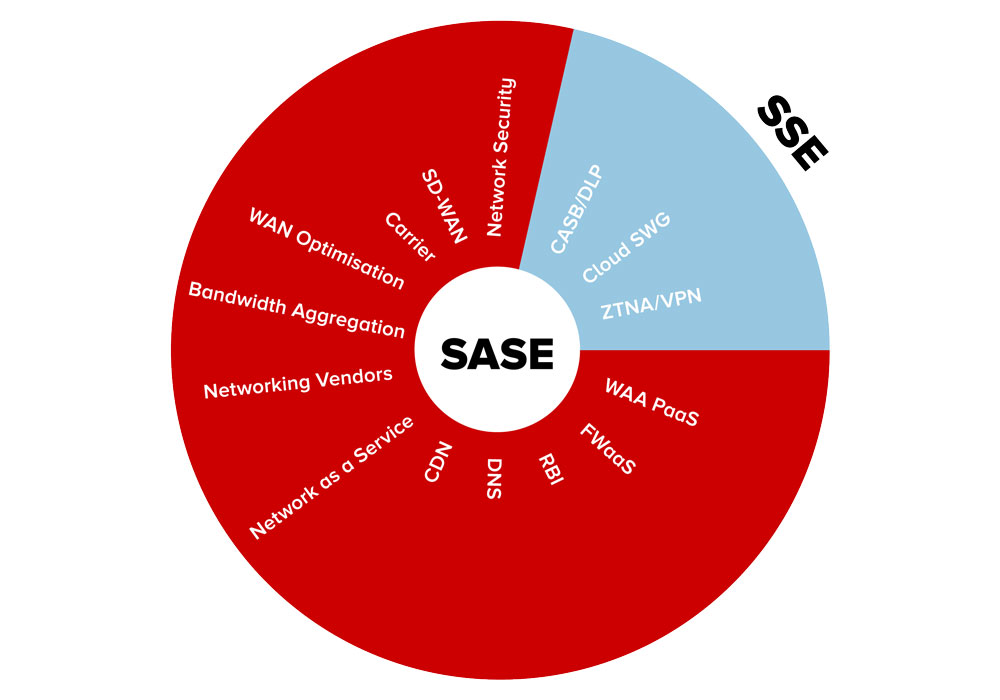
Secure Access Service Edge (SASE) is a dynamic network and security framework, tailored for cloud-driven modern organisations. It combines network security services with WAN capabilities, providing a unified, cloud-native solution. This integration includes Secure Web Gateways (SWG), Zero Trust Network Access (ZTNA), and Firewall-as-a-Service (FWaaS), offering flexibility and scalability.
Leveraging hybrid cloud solutions, SASE excels in secure access and data protection, outperforming traditional on-premises infrastructure. It enhances network security and performance, making it ideal for managing network traffic, user access, and security monitoring, especially for mobile users and branch offices.
Security Service Edge (SSE) adopts a security-centric approach, embedding security within the network infrastructure. Unlike SASE's integrated security and networking services, SSE's focus is on enhancing security services as a core network component. This distinct approach ensures that security is deeply integrated, not merely an additional feature.
SSE delivers robust security measures like next-generation firewalls, intrusion prevention systems (IPS), data loss prevention (DLP), and threat intelligence. These are seamlessly woven into the network fabric, making security a fundamental aspect of the network's architecture. This integration solidifies SSE's role in strengthening network defense.
The fundamental distinction between SASE and SSE lies in their architectural approach. SASE is an integrated framework that combines networking and security services into a unified cloud-native platform. SSE, on the other hand, is focused primarily on embedding security services directly into the network infrastructure.
Both SASE and SSE are focused on enhancing security, but SSE is more intensely concentrated on security services. SSE integrates security throughout every layer of the network, providing a deeply secure approach. While SASE offers a broad range of security measures, it might not match SSE's depth in specific security services.
Choosing between SASE and SSE hinges on your organisation's unique security needs, existing network infrastructure, and strategic objectives:
1. For a cloud-native solution that seamlessly integrates networking and security services, SASE is ideal.
2. SSE suits those prioritizing security embedded within the network architecture.
3. Conduct a comprehensive assessment and consult experts to align your choice—SASE for integrated secure access or SSE for network-centric security—with your goals.
Implementing either SASE or SSE requires careful planning and consideration. SASE deployments often involve transitioning to cloud-based services, which may require a shift in network architecture and security policies. SSE implementations involve integrating advanced security measures into the existing network fabric, which can require specialised expertise.
Cloud Access Security Broker (CASB) is a crucial component in both SASE and SSE frameworks. It serves as a security gateway, managing and securing access to cloud services. CASBs are key in extending security policies beyond traditional network boundaries, crucial for organisations utilising cloud-based resources. They play a significant role in monitoring user access, enforcing data protection protocols, and integrating seamlessly with existing on-premises infrastructure. This function is vital in advanced security monitoring and effective access control, enhancing network security and access optimisation for mobile users and branch offices within SASE and SSE environments.
In the evolving cybersecurity landscape, SASE and SSE are gaining prominence. SASE, with its cloud-centric security capabilities, is increasingly adopted by organisations seeking cloud solutions for secure access and network security. SSE, offering robust security services and data protection, is preferred in sectors like finance, healthcare, and government, where stringent security is paramount. Both strategies provide effective solutions for managing network traffic, ensuring data security, and adapting to the dynamic threat landscape.
The surge in cybercrime, increasing costs per incident (over $39,000 for small, $88,000 for medium, and $62,000 for large businesses)¹, underscores the need for strategic network security choices with enhanced security technologies. SASE and SSE stand out as distinct strategies to protect organisational assets and data. Understanding their fundamental differences and aligning them with your organisation's specific needs is key. Opting for SASE's all-encompassing agility or SSE's robust, targeted defenses can strengthen your network against the evolving landscape of cyber threats.
SASE and SSE cater to distinct network security needs: SASE enables secure, anywhere access to cloud applications, integrating various network and security functions for a streamlined approach. SSE, deployed near data origin, emphasizes strong load balancing and content caching with firewalls or intrusion prevention systems. This differentiation guides organisational focus—SASE on secure access permissions and SSE on network infrastructure security.
Organisations increasingly favor SASE over SSE for providing secure access across various locations and devices. SASE offers a dynamic, cloud-based solution, integrating network security with access control, tailored for a remote workforce. It contrasts with SSE's focus on securing network perimeters and defending against external threats and intrusions.
As reliance on cloud-based applications grows, traditional cybersecurity falls short. SASE and Server-Side Encryption (SSE) technologies enhance user experience and cybersecurity. SASE offers a comprehensive, cloud-delivered solution that merges networking and security, protecting data and applications against cyber threats. SSE adds a layer of server-side encryption, ensuring security without affecting performance. Implementing SASE and SSE helps organisations balance security with user experience, crucial in the digital era.
Carhartt, an American clothing manufacturer, and Prestige Financial exemplify SASE and SSE implementations. Carhartt secured its digital perimeter and maintained performance by integrating network and security policies via a SASE model. Meanwhile, Prestige Financial's SSE architecture reduced operational costs by 48% and enhanced secure remote access, regulatory compliance, and user experience. These cases highlight SASE and SSE's effectiveness in managing network and security challenges with agility and efficiency.
SASE and SSE trends focus on cloud-centric security, emphasising secure access and network security for remote users and mobile devices. These technologies incorporate zero-trust network access, data protection, and security services, enhancing secure web gateway and threat protection. Leveraging cloud access security broker functions, they offer advanced security monitoring and access control, seamlessly integrating with existing on-premises infrastructure and extending security policies to branch offices. These solutions prioritise user access, user behavior network traffic management, and data security, aiming to streamline operations and optimise network performance.