Summary: Despite advances in cyber security technology, human behaviour remains the leading cause of data breaches, accounting for up to 95% of cyber incidents, according to key findings in industry reports.
In this article,
Anthony Porter Canon Business Services ANZ (CBS) explores why people are still the biggest vulnerability in most organisations’ defences, and how they can become your strongest asset.
From phishing attempts, simulations and behavioural nudges to role-specific training and
culture-led strategies, the piece outlines practical ways to close the human gap in
cybersecurity. Anthony shares why CBS focuses on education, enablement, and human risk profiling to build lasting resilience across teams, and why treating human risk with the same rigour as technical risk is essential for any modern security strategy.
Cybersecurity’s biggest blind spot: The human factors and how to address them
Information technology may be advancing fast, but human behavior remains cyber security’s weakest link. Despite billions spent globally on next-gen cybersecurity measures, data breaches continue to originate with a single click, a missed alert, or a moment of misplaced trust.
Despite significant investments in advanced security technologies, human behaviour continues to be a critical weak point in cybersecurity defences. The latest
2025 Verizon Data Breach Investigations Report reveals that nearly 60% of confirmed data breaches involved a human element through error, manipulation, or misuse, underscoring that people, not just systems, remain the most targeted and exploitable facet in breach scenarios.
This aligns with historical data (
2024’s report showed 68%), reflecting sustained risk associated with human interaction across organisational environments. The report uncovered that a staggering
8% of employees were responsible for 80% of human-risk-related cyber incidents highlighting the need for targeted behavioural interventions.
The message is clear:
you can’t patch human nature.
The human element in cybersecurity
“
Cybersecurity has always been a race between technology and human behaviour,” says Anthony Porter, Cloud Security Architect at Canon Business Services ANZ. “And humans remain the most unpredictable variable.”
Cyber attackers have long understood that the easiest way into a secure system isn’t through the firewall, it’s through people. Social engineering attacks exploit our most natural instincts: curiosity, trust, urgency, even helpfulness. And it works.
“Even with
AI-augmented monitoring in place, a well-timed phishing attack or shared credential can unravel the most advanced defences,” Anthony notes. “Security incidents are increasingly less about technological sophistication and more about manipulating human behaviour.”
Why security culture lags behind
If the risk is so well understood, why are the vast majority of organisations still under-investing in the human element?
Part of the problem, says Anthony, is visibility. “Technical vulnerabilities are easy to scan, track, and remediate. Human risk is harder to measure and harder to prove ROI on.”
This often results in cybersecurity awareness being treated as a compliance exercise: annual training sessions, static slide decks, and tick-box reporting. Meanwhile, real-world behaviour—sharing passwords, ignoring
MFA, clicking suspicious links, remains unchanged.
There’s also a cultural challenge. “Many employees see security as someone else’s job,” Anthony says. “And leadership often assumes that tech tools will compensate for human mistakes or insider threats. But technology can only alert you to the risk. It can’t stop someone from clicking send.”
Add to this the pressure on time-poor staff, and cybersecurity training can feel more like a distraction than a priority. Yet, the consequences of neglect are significant. In 2024,
Mimecast’s State of Human Risk Report found that a staggering
95% of data breaches involved human error, with the average cost of an insider-driven data exposure reaching $13.9 million.
Get in touch
Talk to us today to optimise your operations.
Bridging the gap between people and protection
Changing human behaviour isn’t easy. But it is possible with the right mix of psychology, technology, and culture.
“
Forward-thinking security teams cybersecurity professionals are shifting from fear-based messaging to behaviourally informed engagement,” Anthony explains. “They understand that people aren’t purely rational actors. Small nudges can make a big difference.”
Examples include:
- Nudges: Real-time prompts encouraging MFA, flagging sensitive information, or warning users before risky actions.
- Gamification: Turning cybersecurity awareness into a competitive or reward-based exercise, particularly effective for younger cohorts.
- Positive reinforcement: Rewarding secure behaviour instead of just punishing mistakes.
Anthony also notes the value of micro-learning—ongoing, short-form employee training integrated into daily workflows. “Annual training sessions don’t cut it anymore. You need just-in-time education, ideally delivered at the moment of risk.”
Importantly, not all users respond to the same approach. “Some respond to peer-based recognition. Others want traditional group learning. Tailoring the message to different audiences is critical to long-term cultural change.”
Practical strategies to reduce human risk
So how can organisations turn these human factors in cybersecurity from a liability into an asset? Anthony suggests a layered approach that combines security measures and controls with cultural investment.
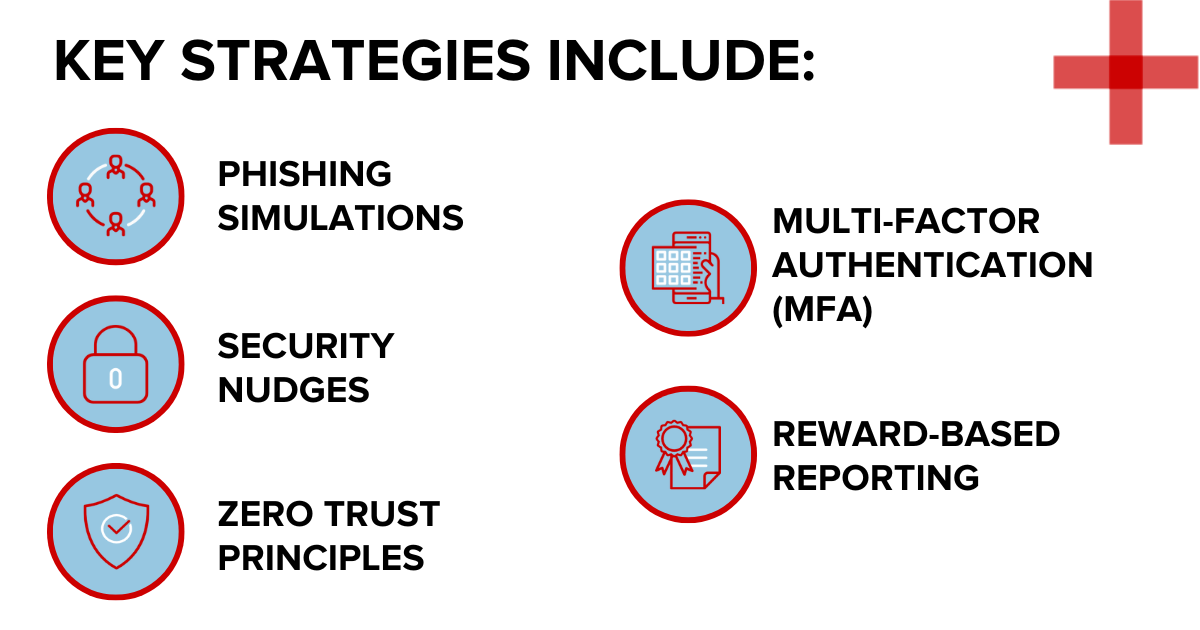
Ongoing education and training also help prevent users from falling victim to phishing emails or suspicious attachments, two common causes of potential breaches.
Importantly, these strategies should not exist in isolation. “The most effective cybersecurity measures are the ones that integrate security into the rhythm of work—subtle, continuous, and context-aware,” Anthony says.
As for success stories? He notes that while many CBS clients outsource aspects of cybersecurity awareness and training, the human element remains difficult to quantify. “Real change isn’t always visible in dashboards. It’s the absence of cybersecurity incidents caused, the quiet shift in behaviour, the moment someone stops and asks before sending.”
Avoiding security fatigue
One growing risk in the push for cybersecurity awareness is security fatigue, where employees feel overwhelmed, disengaged, or simply tune out.
To avoid this, Anthony recommends three key principles:
- Make it relevant: Use storytelling and real-world examples instead of abstract scenarios or static content.
- Keep it simple: Policies should be clear, concise, and easy to apply.
- Deliver it when it matters: Use real-time interventions or post-incident debriefs, not just annual refreshers.
To support engagement and compliance with cybersecurity protocols, forward-thinking teams also introduce positive reinforcement and make information security relatable.
“People relate to people,” he says. “When they understand how a breach happened—or almost happened—they’re more likely to change their behaviour.”
CBS’ approach to human-centric cybersecurity
Canon Business Services ANZ takes a multi-dimensional approach to human risk, combining education,
behavioural analytics, and secure technology enablement.
“We recognise that technology alone can’t fix the human gap,” explains Anthony. “Our role is to make security intuitive, contextual, and aligned with each organisation’s culture, with strong technical controls that support secure actions.”
CBS offerings include:
- Role-specific training programs for executives, frontline teams, and developers, recognising that each group faces unique cybersecurity risks.
- Human risk assessments to identify behavioural patterns and align interventions with key risk factors accordingly.
- Integrated cybersecurity awareness campaigns combining phishing simulations, micro-learning, and cultural reinforcement.
- Tool enablement that ensures cybersecurity platforms support, not hinder, user behavior and experience.
Perhaps most importantly, CBS doesn’t treat security as a bolt-on. “Our philosophy is that culture is the ultimate control,” says Anthony. “If your people see security as enabling their work, not blocking it, you’ve already won half the battle.”
Your people are your perimeter
If Anthony had one piece of advice for CIOs, CISOs and other decision makers, it’s this: “Treat human risk with the same rigour as technical risk. Invest in understanding human behaviour, not just deploying tools.”
Ultimately, people aren’t the weakest link. They’re your most underutilised defence. “When empowered, staff can be just as effective as any tool in detecting cyber attacks, from ransomware attacks to credential harvesting. They create a culture where security becomes everyone’s responsibility,” he says.
As cyber threats become more sophisticated, the key differentiator won’t be technology alone. It will be how well your people are equipped to recognise, respond to, and prevent cybersecurity threats before they ever reach your firewall.
To learn how Canon Business Services helps customers to uplift security and what discovery workshops we have available, contact us today. for valuable insights into your most important layer of defence: your people.
