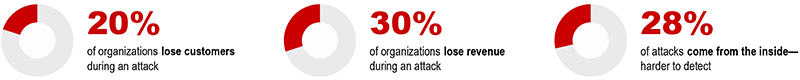
With ever-evolving cyber threats year-on-year, IT and cybersecurity must be a focus for all organisations. If you aren’t yet convinced of how devastating an attack can be, just look at the extensive list of notable breaches that occurred in 2022, from Optus and Medibank, to Bunnings and Telstra.
No company can truly say that they aren’t at risk of an attack. Given the way cybersecurity threats have evolved, SME targets can be just as appealing as enterprise organisations—in fact, they represent a growing number of data breach reports. The Australian Cyber Security Centre (ACSC) Small Business Survey, for example, reports that “62 per cent of respondents have experienced a cyber security incident.” Interestingly, almost half of participants reported spending 'less than $500 per year' on their cyber defenses. This raises the question of whether investing in Cyber Security Services might be a wise choice for enhanced protection.
To assess how your current security posture stacks up—and to avoid becoming this year’s big news headline—use our IT security checklist to strengthen your systems as we continue into the future. Not only can taking these steps reduce your risk, but doing so may also help you to reduce your cybersecurity insurance premiums, if you’ve seen the cost of your cover soar recently.
Of course, some of these items may not apply to you, depending on your organisation’s type, size, geographic region, or industry. If you need help assessing your company’s specific vulnerabilities, reach out to Canon Business Services (CBS) for help with a customised security assessment.
To build a strong security program, you need to understand the environment you’re working in. That’s why it’s important to begin by assessing your environment and documenting all of the following assets or elements:
Depending on the specifics of your situation, it may also be a good idea to:
Next, when it comes to managing the security of your technology, make sure you can tick each of the following boxes. If you can’t, take action to do so ASAP, either on your own or with the support of an external partner.
Truly, your systems are only as secure as the people working within them. In addition to securing your technology, invest in educating all of your company’s users on proper security behaviours. Can you tick each of the following boxes?
Transform Your Cyber Defense: Prioritised Actions for Staying Ahead of Threats.
DownloadFinally, keep in mind that security is not a ‘one-and-done’ activity. To maintain protection once you’ve established practices that govern the security of your technology and people, establish ongoing processes that tick each of the following boxes:
If our IT security checklist sounds like a lot, that’s because it’s meant to. Even as security management has become more complex than ever, it’s become more important than ever for companies of every size.
So if you aren’t sure what any of these items mean—or if you aren’t sure how to implement them on your own—CBS can help. Reach out to our team for a personalised assessment of your security needs or for expert support uplifting your security in 2024.
Canon Business Services ANZ (CBS) is proud to be among the few Australian MSSPs in the Microsoft Intelligent Security Association (MISA), which means we can better defend you against a world of increasing cyber threats. Choose the team with 3 Azure advanced security specialisations (Identity & Access Management, Cloud Security and Threat Protection) to safeguard your organisation today.
A cloud security checklist is essential to evaluate the security posture of a cloud environment. It incorporates best practices for securing sensitive data, including proper encryption and access controls. The checklist assesses cloud infrastructure, security controls, and network security.
Regular patches and updates should be part of the checklist to mitigate security risks, and multi-factor authentication should be implemented for secure cloud access. In case of security incidents or data breaches, an incident response plan should be in place, ensuring real-time incident detection and data recovery.
The cloud security assessment checklist is a comprehensive guide that combines policies and procedures to assess a cloud-based environment's overall security. It emphasizes the importance of data classification and protection, with encryption keys playing a significant role.
Data access should be closely monitored, and a cloud provider's security controls should align with the latest security best practices. Security awareness is crucial to prevent security incidents, and a response plan should be ready to address any security breaches, including third-party involvement.
A critical aspect of a cloud security checklist is protecting data in a cloud environment. Best practices for cloud security should include securing sensitive data with encryption and strong access controls.
Regularly applying patches and updates can help mitigate security risks. Multi-factor authentication adds an extra layer of security to cloud access. An incident response plan is crucial to address security incidents and data breaches in real time. Cloud-based data recovery is part of an overall security strategy.
The cloud security assessment checklist is a tool to evaluate the security posture of a cloud environment. It encompasses best practices for securing sensitive data, employing encryption keys, and implementing identity and access management (IAM).
The checklist covers security controls, network security, and the importance of keeping up with the latest security best practices through patches and updates. Multi-factor authentication is a key component to protect data in the cloud. In the event of security incidents or data breaches, an incident response plan should be in place to respond in real-time and recover data.